20250617 UPDATE:
mosdns比较依赖于上游DNS,尤其是现在国外DNS间歇性阻断,导致使用体验很差需要定期对上游DNS进行更新,使用成本较高,故下面配置不再维护。
推荐使用PaoPaoDNS + AdGuard Home
mosdns和tpclash实现DNS防泄露和DNS防污染,如果要实现上述两种效果请使用nameserver修改版 请使用本地配置版,想要什么配置只需要修改/data/clash_config/default_config.yaml,本人使用为Debian10.
优点:没有openclash和openwrt花里胡哨,省心
缺点:规则需要放在github上,稍微有点麻烦
使用方法:1. 开系统代理,mixed端口7890,socks端口7891。
2. 改路由IP为这个IP,但是DNS要胡填一个,否则分流会失败。
2. Web-ui的密码是tpclash。
1. tpclash
tpclash已删库,下载链接:mega
安装tpclash
1
2
| chmod u+x tpclash
./tpclash install
|
可执行文件位置:/usr/local/bin/tpclash 与 /usr/local/bin/tpclash.sh
本地配置文件:/etc/clash.yaml
修改clash.yaml
远程配置文件
修改:vim /usr/local/bin/tpclash.sh
1
2
3
| #!/usr/bin/bash
/usr/local/bin/tpclash --auto-fix tun -i "60m" -c "https://example.com/clash.yaml"
|
卸载tpclash
1
2
| systemctl stop tpclash
tpclash uninstall
|
命令
1
2
3
4
5
6
7
8
| 重载配置
systemctl daemon-reload
启动
systemctl start tpclash
重启
systemctl restart tpclash
开机自启
systemctl enable tpclash
|
常用命令
1
2
3
4
5
6
7
8
| systemctl start tpclash
systemctl status tpclash
systemctl stop tpclash
systemctl restart tpclash
systemctl enable tpclash
systemctl disable tpclash
journalctl -fu tpclash
systemctl daemon-reload
|
2. mosdns
release: https://github.com/IrineSistiana/mosdns/releases
wiki: https://irine-sistiana.gitbook.io/mosdns-wiki/mosdns-v5
创建相关配置文件
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
| cp mosdns /usr/local/bin/
mkdir -p /etc/mosdns/rules
touch config.yaml
mv config.yaml /etc/mosdns/
touch /etc/mosdns/rules/anti-ad-domains.txt
touch /etc/mosdns/rules/cn.txt
touch /etc/mosdns/rules/direct-list.txt
touch /etc/mosdns/rules/hosts
touch /etc/mosdns/rules/custom_for_cndns.txt
touch /etc/mosdns/rules/custom_for_worlddns.txt
touch /etc/mosdns/rules/ddnslist.txt
touch /etc/mosdns/rules/custom_black_list.txt
touch /etc/mosdns/rules/custom_for_jp_edns.txt
touch /etc/mosdns/rules/custom_for_us_edns.txt
|
运行测试一次:
1
| /usr/local/bin/mosdns start -c /etc/mosdns/config.yaml -d /etc/mosdns
|
更新rules
1
2
3
4
5
6
7
8
| sudo tee > /etc/mosdns/rules/update_rules <<'EOF'
mirror_proxy=""
mosdns_working_dir="/etc/mosdns"
mkdir -p /tmp/mosdns && curl ${mirror_proxy}https://raw.githubusercontent.com/Loyalsoldier/v2ray-rules-dat/release/direct-list.txt > /tmp/mosdns/direct-list.txt && curl ${mirror_proxy}https://raw.githubusercontent.com/privacy-protection-tools/anti-AD/master/anti-ad-domains.txt > /tmp/mosdns/anti-ad-domains.txt && curl ${mirror_proxy}https://raw.githubusercontent.com/Loyalsoldier/geoip/release/text/cn.txt > /tmp/mosdns/cn.txt && \cp -rf /tmp/mosdns/*.txt ${mosdns_working_dir}/rules && rm -rf /tmp/mosdns/* && echo 'update successful'
mosdns service restart
EOF
|
1
2
3
4
5
6
7
8
9
| chmod u+x /etc/mosdns/rules/update_rules
/etc/mosdns/rules/update_rules
crontab -e
0 4 * * * /etc/mosdns/rules/update_rules
|
新建服务
位于/etc/systemd/system/mosdns.service
1
2
3
4
5
6
7
8
9
10
11
12
13
| sudo tee > /etc/systemd/system/mosdns.service <<'EOF'
[Unit]
Description=mosdns daemon, DNS server.
After=network-online.target
[Service]
Type=simple
Restart=always
ExecStart=/usr/local/bin/mosdns start -c /etc/mosdns/config.yaml -d /etc/mosdns
[Install]
WantedBy=multi-user.target
EOF
|
常用命令
1
2
3
4
5
6
7
| systemctl daemon-reload
systemctl enable mosdns
systemctl start mosdns
systemctl restart mosdns
systemctl status mosdns
journalctl -fu mosdns
tail -f /etc/mosdns/mosdns.log
|
可以实现白名单使用国内DNS,白名单外使用国外DNS,如果使用国外CDN返回的结果为国内IP,则使用国内DNS重新解析,避免DNS泄露与污染。
国外版mosdns config.yaml,国内版mosdns只需要将国外的DNS地址换成可用的纯净的DNS地址即可。推荐doh.apad.pro和dns.66a.net。
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
192
193
194
195
196
197
198
199
200
201
202
203
204
205
206
207
208
209
210
211
212
213
214
215
216
217
218
219
220
221
222
223
224
225
226
227
228
229
230
231
232
233
234
235
236
237
238
239
240
241
242
243
244
245
246
247
248
249
250
251
252
253
254
255
256
257
258
259
260
261
262
263
264
265
266
267
268
269
270
271
272
273
274
275
276
277
278
279
280
281
282
283
284
285
286
287
288
289
290
291
292
293
294
295
296
297
298
299
300
301
302
303
304
305
306
307
308
309
310
311
312
313
314
315
316
317
318
319
320
321
322
323
324
325
326
327
328
329
330
331
332
333
334
335
336
337
338
339
340
341
342
343
344
345
346
347
348
349
350
351
352
353
354
355
356
357
358
359
360
361
362
363
364
365
366
367
368
369
370
371
372
373
374
375
376
377
378
379
380
381
382
383
384
385
386
387
388
389
390
391
392
393
394
395
396
397
398
399
400
401
402
| log:
level: error
production: true
file: "./mosdns.log"
plugins:
- tag: cn_domainList
type: "domain_set"
args:
files:
- "./rules/direct-list.txt"
- "./rules/custom_for_cndns.txt"
- tag: block_domains
type: "domain_set"
args:
files:
- "./rules/anti-ad-domains.txt"
- "./rules/custom_black_list.txt"
- tag: custom_world_list
type: "domain_set"
args:
files:
- "./rules/custom_for_worlddns.txt"
- tag: jp_edns_list
type: "domain_set"
args:
files:
- "./rules/custom_for_jp_edns.txt"
- tag: us_edns_list
type: "domain_set"
args:
files:
- "./rules/custom_for_us_edns.txt"
- tag: ddnslist
type: "domain_set"
args:
files:
- "./rules/ddnslist.txt"
- tag: cn_ipList
type: "ip_set"
args:
files:
- "./rules/cn.txt"
- tag: ecs_DNS
type: "forward"
args:
upstreams:
- tag: google_doh
addr: "https://dns.google/dns-query"
bootstrap: "8.8.8.8"
enable_pipeline: true
insecure_skip_verify: false
- tag: google_dot
addr: "tls://dns.google"
bootstrap: "8.8.8.8"
enable_pipeline: true
insecure_skip_verify: false
- tag: world_DNS
type: "forward"
args:
concurrent: 2
upstreams:
- tag: cloudflare_doh
addr: "https://one.one.one.one/dns-query"
dial_addr: "1.0.0.1"
bootstrap: "8.8.8.8"
enable_pipeline: true
insecure_skip_verify: false
- tag: quad9_dot
addr: "tls://dns10.quad9.net"
bootstrap: "8.8.8.8"
enable_pipeline: true
insecure_skip_verify: false
- tag: opendns_doh
addr: "https://doh.opendns.com/dns-query"
bootstrap: "8.8.8.8"
enable_pipeline: true
insecure_skip_verify: false
- tag: cn_DNS
type: "forward"
args:
concurrent: 2
upstreams:
- tag: OneDNS
addr: "udp://52.80.52.52"
enable_pipeline: true
insecure_skip_verify: false
- tag: CNNIC_SDNS
addr: "udp://1.2.4.8"
enable_pipeline: true
- tag: OneDNS_dot
addr: "tls://dot-pure.onedns.net"
bootstrap: "223.6.6.6"
enable_pipeline: true
insecure_skip_verify: false
- tag: DNSπ
addr: "tls://101.226.4.6"
enable_pipeline: true
insecure_skip_verify: false
- tag: cn_fallback_DNS
type: "forward"
args:
concurrent: 2
upstreams:
- tag: dnspod_doh
addr: "https://doh.pub/dns-query"
bootstrap: "223.6.6.6"
enable_pipeline: true
insecure_skip_verify: false
- tag: 360_doh
addr: "https://doh.360.cn/dns-query"
enable_pipeline: true
- tag: ali_dot
addr: "tls://223.5.5.5"
insecure_skip_verify: false
- tag: easymosdns_doh
addr: "https://doh.apad.pro/dns-query"
bootstrap: "223.6.6.6"
enable_pipeline: true
insecure_skip_verify: false
- tag: cache
type: "cache"
args:
size: 65535
dump_file: "./cache.dump"
lazy_cache_ttl: 86400
dump_interval: 600
- tag: custom_hosts
type: "hosts"
args:
files:
- "./rules/hosts"
- tag: modify_ddns_ttl
type: "sequence"
args:
- exec: ttl 1-5
- tag: modify_ttl
type: "sequence"
args:
- exec: ttl 5-10
- tag: modify_black_ttl
type: "sequence"
args:
- exec: ttl 600-3600
- tag: modify_resp_ttl
type: "sequence"
args:
- matches: qname $ddnslist
exec: mark 123
- matches: qname $block_domains
exec: mark 456
- matches: mark 123
exec: jump modify_ddns_ttl
- matches: mark 456
exec: jump modify_black_ttl
- matches:
- "!mark 123"
- "!mark 456"
exec: jump modify_ttl
- tag: world_resolve
type: "sequence"
args:
- exec: $world_DNS
- exec: jump modify_resp_ttl
- exec: query_summary world_DNS
- matches: "has_resp"
exec: accept
- tag: cn_resolve
type: "sequence"
args:
- exec: ecs 123.112.0.0
- exec: $cn_DNS
- exec: jump modify_resp_ttl
- exec: query_summary cn_DNS
- tag: cn_fallback_resolve
type: "sequence"
args:
- exec: ecs 123.112.0.0
- exec: $cn_fallback_DNS
- exec: jump modify_resp_ttl
- exec: query_summary cn_fallback_DNS
- tag: ecs_jp_resolve
type: "sequence"
args:
- exec: ecs 1.5.0.0
- exec: $ecs_DNS
- exec: jump modify_resp_ttl
- exec: query_summary ecs_jp_resolve
- matches: "has_resp"
exec: accept
- tag: ecs_us_resolve
type: "sequence"
args:
- exec: ecs 4.80.0.0
- exec: $ecs_DNS
- exec: jump modify_resp_ttl
- exec: query_summary ecs_us_resolve
- matches: "has_resp"
exec: accept
- tag: ecs_cn_resolve
type: "sequence"
args:
- exec: ecs 123.112.0.0
- exec: $ecs_DNS
- exec: jump modify_resp_ttl
- exec: query_summary ecs_cn_resolve
- matches: "has_resp"
exec: accept
- tag: match_block_domain
type: "sequence"
args:
- exec: black_hole 127.0.0.1 ::1 0.0.0.0
- exec: query_summary block_domains
- tag: custom_hosts_resp
type: "sequence"
args:
- exec: jump modify_resp_ttl
- matches: "has_resp"
exec: query_summary custom_hosts
- matches: "has_resp"
exec: accept
- tag: hit_cache_resp
type: "sequence"
args:
- exec: jump modify_resp_ttl
- matches: "has_resp"
exec: query_summary hit_cache
- matches: "has_resp"
exec: accept
- tag: query_is_reject
type: "sequence"
args:
- matches: "qname $block_domains"
exec: jump match_block_domain
- matches: qtype 65
exec: reject 5
- matches: "has_resp"
exec: accept
- tag: fallback_world
type: "fallback"
args:
primary: ecs_cn_resolve
secondary: world_resolve
threshold: 1500
always_standby: false
- tag: fallback_cn
type: "fallback"
args:
primary: cn_resolve
secondary: cn_fallback_resolve
threshold: 2000
always_standby: false
- tag: fallback_cn_seq
type: "sequence"
args:
- exec: $fallback_cn
- matches: "resp_ip $cn_ipList"
exec: accept
- tag: fallback_world_seq
type: "sequence"
args:
- exec: $fallback_world
- matches: "has_resp"
exec: accept
- tag: resolve_process
type: "sequence"
args:
- exec: prefer_ipv4
- exec: $custom_hosts
- matches: "has_resp"
exec: goto custom_hosts_resp
- matches: "!qname $ddnslist"
exec: $cache
- matches: "has_resp"
exec: goto hit_cache_resp
- matches: "qname $jp_edns_list || github.com"
exec: jump ecs_jp_resolve
- matches: "qname $us_edns_list"
exec: jump ecs_us_resolve
- matches: "qname $custom_world_list || $ddnslist"
exec: goto fallback_world_seq
- exec: jump query_is_reject
- matches: "qname $cn_domainList"
exec: jump fallback_cn_seq
- exec: goto fallback_world_seq
- tag: udp_server
type: "udp_server"
args:
entry: resolve_process
listen: "127.0.0.1:53"
- tag: tcp_server
type: "tcp_server"
args:
entry: resolve_process
listen: "127.0.0.1:53"
- tag: server_http
type: "http_server"
args:
entries:
- path: /dns-query
exec: resolve_process
src_ip_header: "X-Real-IP"
listen: 127.0.0.1:4588
cert: ""
key: ""
idle_timeout: 10
|
建议国内域名解析使用国内服务器进行解析,否则有时就算加上edns解析出来还是国外IP。
国外mosdns和国内mosdns配置的区别在于,国外的IP使用国内知名DNS解析国内域名有可能会获取到国外的节点,会使访问速度变慢,所以国外mosdns要使用非知名DNS解析来获取国内域名IP。
建议使用国内mosdns(可以使用DOT)和国外mosdns(只能使用DOH)搭配使用,国内的负责解析国内域名(速度快),国外的负责无污染的域名解析(安全)。
如果本地搭建的话请使用DoT、DoH等加密方式。
PS. DoT 853端口活了不到2个小时,建议拿国内服务器中转。
安卓的私人DNS需要使用DoT。
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
| server
{
listen 443 ssl http2;
server_name domain;
ssl_certificate crt;
ssl_certificate_key key;
location /dns-query {
proxy_pass http://127.0.0.1:4588/dns-query;
proxy_set_header X-Real-IP $remote_addr;
access_log /www/wwwlogs/dns-query.log;
error_log /www/wwwlogs/dns-query.err.log;
}
}
|
域名匹配规则
以 domain: 开头,域匹配。e.g: domain:google.com 会匹配自身 google.com,以及其子域名 www.google.com, maps.l.google.com 等。
以 full: 开头,完整匹配。e.g: full:google.com 只会匹配自身。
以 keyword: 开头,关键字匹配。e.g: keyword:google.com 会匹配包含这个字段的域名,如 google.com.hk, www.google.com.hk。
以 regexp: 开头,正则匹配(Golang 标准)。e.g: regexp:.+\.google\.com$。
匹配方式按如下顺序生效: full > domain > regexp > keyword。
性能:
domain 和 full 匹配使用 HashMap,复杂度 O(1)。每 1w 域名约占用 1M 内存。
keyword 和 regexp 匹配需遍历,复杂度 O(n)。
PS. tun模式tpclash会自动开启转发
1
| echo 1 > /proc/sys/net/ipv4/ip_forward
|
3. 效果
https://browserleaks.com/dns
https://www.dnsleaktest.com/
https://ipleak.net/
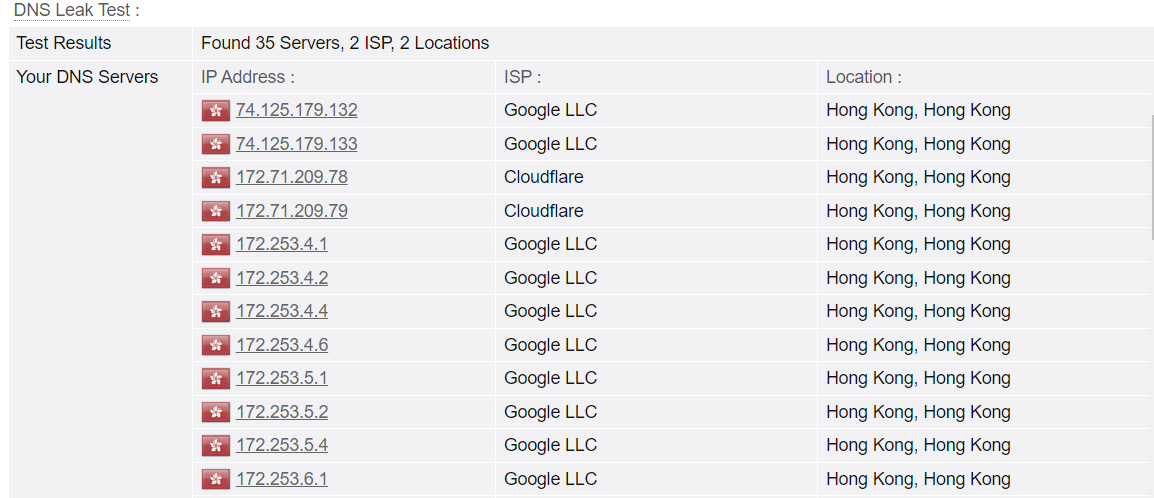
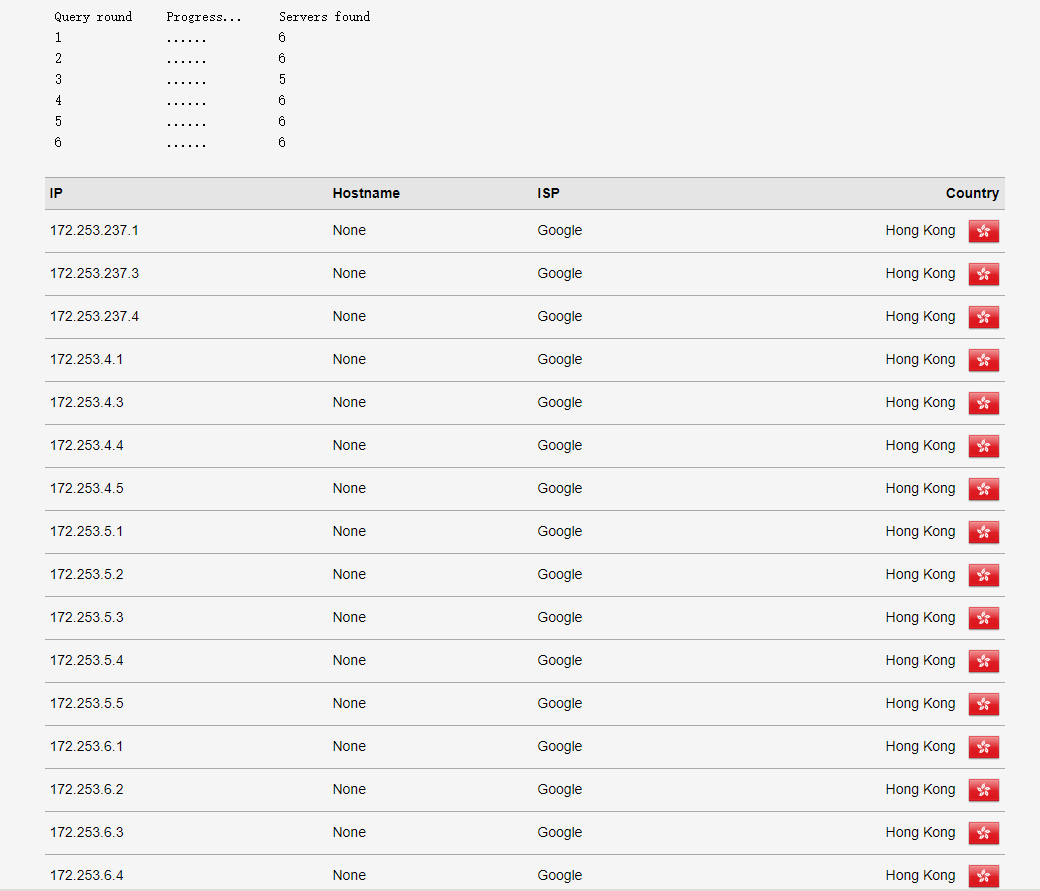
4. 国内外常用DNS
国内
腾讯 DNS
支持 ECS
1
2
3
4
5
6
7
8
| IPv4: 119.29.29.29
DoH: https:
DoH: https:
DoH: https:
DoH: https:
DoT: tls:
DoT: tls:
DoT: tls:
|
阿里 DNS
支持 ECS
1
2
3
4
5
6
| IPv4: 223.5.5.5
IPv4: 223.6.6.6
DoH: https:
DoH: https:
DoH: https:
DoT: tls:
|
CNNIC SDNS
Only UDP
国外服务器解析得到国内IP
DNS 派
支持ECS、DoT
1
2
3
4
5
| IPv4: 101.226.4.6
IPv4: 218.30.118.6 (电信/移动/铁通)
IPv4: 123.125.81.6
IPv4: 140.207.198.6 (联通)
DoT: tls:
|
oneDNS
https://www.onedns.net/personal
1
2
3
4
5
6
7
| IPv4: 52.80.66.66
IPv4: 52.80.66.66
IPv4: 117.50.11.11 (不稳定)
DoT: tls://dot-pure.onedns.net (纯享版)
DoT: tls://dot.onedns.net (拦截版)
DoH: https://doh.onedns.net/dns-query
DoH: https://doh-pure.onedns.net/dns-query
|
EasyMosdns
https://apad.pro/dns-doh/
【境内域名】使用AliDNS本地查询,部分域名使用DNSPod补充查询
【境外域名】使用GoogleDNS与CloudflareDNS通过加密隧道远程查询
无污染、支持EDNS,解析精准度极高,IP分流远程加密查询上游DNS,保护隐私,境外域名拦截垃圾广告,境内域名无拦截,多级DNS缓存,加速全球域名查询响应。
国外
Cloudflare DNS
1
2
3
4
5
6
7
8
9
10
| IPv4: 1.0.0.1
IPv4: 1.1.1.1
DoH: https:
DoH: https:
DoH: https:
DoH: https:
DoT: tls:
DoT: tls:
DoT: tls:
DoT: tls:
|
Google DNS
支持EDNS
1
2
3
4
5
6
7
8
| IPv4: 8.8.8.8
IPv4: 8.8.4.4
DoH: https:
DoH: https:
DoH: https:
DoT: tls:
DoT: tls:
DoT: tls:
|
IBM Quad9
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
| #推荐:Malware Blocking、DNSSEC Validation(这是最典型的配置)
IPv4: 9.9.9.9
IPv4: 149.112.112.112
DoH: https:
DoT: tls:
DoT: tls:
#使用 ECS 保护:恶意软件阻止、DNSSEC 验证、启用 ECS
IPv4: 9.9.9.11
IPv4: 149.112.112.11
DoH: https:
DoT: tls:
DoT: tls:
#不安全:没有恶意软件阻止,没有 DNSSEC 验证(仅限专家!)
IPv4: 9.9.9.10
IPv4: 149.112.112.10
DoH: https:
DoT: tls:
DoT: tls:
|
OpenDNS
1
2
3
4
5
| IPv4: 208.67.222.222
IPv4: 208.67.220.220
DoH: https:
DoH: https:
DoT: tls:
|
AdGuard DNS
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
| #无过滤,不拦截
IPv4: 94.140.14.140
IPv4: 94.140.15.15
DoH: https:
DoT: tls:
DoQ: quic:
#过滤广告和跟踪
IPv4: 94.140.14.14
IPv4: 94.140.15.15
DoH: https:
DoT: tls:
DoQ: quic:
#家庭过滤:开启安全搜索和安全模式选项、拦截成人内容,并且屏蔽广告和跟踪器
IPv4: 94.140.14.15
IPv4: 94.140.15.16
DoH: https:
DoT: tls:
DoQ: quic:
|
5. 参考或引用
https://irine-sistiana.gitbook.io/mosdns-wiki/mosdns-v5
https://blog.0ne.day/i/mosdns-dns-c-0KfHuTo35/
https://hgl2.com/2023/install-mosdns-in-macos/
https://github.com/Loyalsoldier/v2ray-rules-dat/tree/release
https://github.com/privacy-protection-tools/anti-AD
https://github.com/Loyalsoldier/geoip/tree/release/text
https://github.com/pmkol/easymosdns
https://ip.cn/dns.html
https://www.cccitu.com/2205354.html
https://github.com/kkkgo/PaoPaoDNS
https://github.com/pmkol/easymosdns

